Bread without commercial yeast - Sour-dough
At the time of writing, an extraordinary number of people are in some sort of lockdown, and trying to go the shops less often, and when they do, certain items are in short supply. One of those items is commercial yeast. If you still have access to flour (preferably strong flour), salt and water, you […]
Battleships Server / Client for Education
I've been teaching a first year introductory module in Python programming for Engineering at Ulster University for a few years now. As part of the later labs I have let the students build a battleships game using Object Oriented Programming - with "Fleet" objects containing a list of "Ships" and so on where they could […]
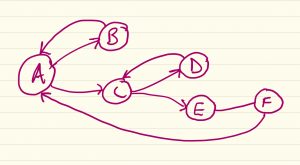
Anatomy of a Puzzle
Recently I was asked to provide a Puzzle For Today for the BBC Radio 4 Today programme which was partially coming as an Outside Broadcast from Ulster University. I've written a post about the puzzle itself, and some of the ramifications of it; this post is really more about the thought process that went into […]
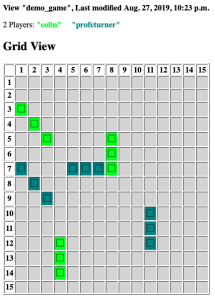
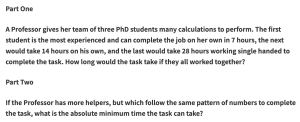
My Puzzle for the Day
In November 2018 the BBC Radio 4 Today Programme was visiting Ulster University for an outside broadcast. I was asked to write the Puzzle for the Day for the broadcast. Here is my puzzle and some discussion about how it can be solved. The puzzle and a very brief solution is on the BBC page, […]
Review: The Very Short Introduction
Infinity, A Very Short Introduction, by Ian Stewart This review was originally written for the London Mathematical Society November 2018 Newsletter. The book can be found here. The “Very Short Introduction” series by Oxford University Press attempt to take a moderately deep dive into various subjects in a slimline volume. Professor Stuart addresses the apparent […]
Implementing configurable work-flow patterns in Python Django
In my previous article, I discussed some of changes I've made to my WAM software to handle assessment and work-flow. I thought I'd have a look at this from the technical side for those interested in doing something similar, this is obviously extensible to general workflow management, where you might want to tweak the workflow […]
Assessment handling and Assessment Workflow in WAM
Sometime ago I began writing a Workload Allocation Modeller aimed at Higher Education, and I've written some previous blog articles about this. As is often the way, the scope of the project broadened and I found myself writing in support for handling assessments and the QA processes around them. At some point this necessitates a […]
Migrating Django Migrations to Django 2.x
Django is a Python framework for making web applications, and its impressive in its completeness, flexibility and power for speedy prototyping. It's also an impressive project for forward planning, it has a kind of built in "lint" functionality that warns about deprecated code that will be disallowed in future versions. As a result when Django […]
Semi Open Book Exams
A few years ago, I switched one of my first year courses to use what I call a semi-open-book approach. Open-book exams of course allow students to bring whatever materials they wish into them, but they have the disadvantage that students will often bring in materials that they have not studied in detail, or even […]
The Most Dangerous Idea in History
In the modern world we often throw around the word meme to mean some comic image, video or idea that has become associated with a concept, but the word has a different origin. "an element of a culture or system of behaviour passed from one individual to another by imitation or other non-genetic means." This […]